Proxy Settings
This page allows you to configure the proxy server used by features Check for Updates, Downloader and Crash Dump Uploader. In most cases you don't need to make any changes, as defaults will work on majority of installations.
When Hex Editor Neo establishes a connection to remote server, it always does it over HTTP protocol over the 80 port. If your computer must use HTTP proxy when accessing HTTP resources, you may configure the proxy settings on this page. In addition, if your proxy server requires authentication, you may also configure credentials to use.
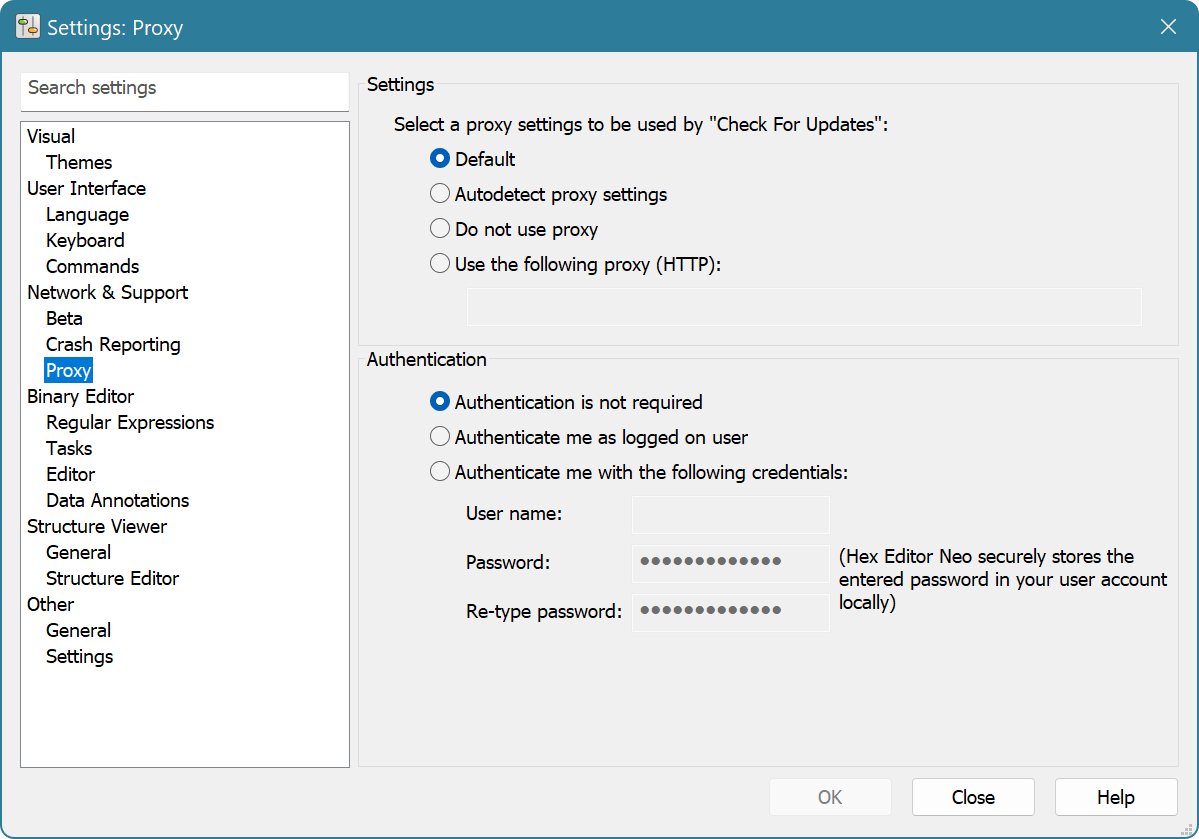
Server Settings
There are four options you can use to configure a proxy server:
- Default
- Hex Editor Neo will use the proxy server configured in your default browser. This is a default setting.
- Autodetect proxy settings
- Hex Editor Neo will try to automatically detect proxy server settings.
- Do not use proxy
- Hex Editor Neo will bypass any configured proxy.
- Use the following proxy (HTTP):
Specify the address (and optionally port number) of the proxy server to use. Examples:
myserver.comwill use the HTTP proxy server myserver.com on port 80 (the default).
myserver.com:8080will use the HTTP proxy server myserver.com on port 8080
Proxy Server Authentication
There are three authentication options you can use:
- Authentication is not required
- Proxy Server does not require authentication.
- Authenticate me as logged on user
- Hex Editor Neo will use the currently logged on user to authenticate on the proxy server.
- Authenticate me with the following credentials:
- Enter the user name and password. You must enter the same password in both Password and Re-type password boxes. See the Security Considerations section below.
Security Considerations
When you configure the Hex Editor Neo to use the entered credentials, it stores entered password in registry under the HKEY_CURRENT_USER key. It uses encryption to store the password. Only the same user is able to decrypt the password.
That is, if encrypted password is copied to another computer, an attacker will not be able to get the plain text password.